Barely a week goes by without news of another company or public agency affected by data breaches, ransomware, or other forms of cyberattack. Last year, in fact, the Federal Bureau of Investigation’s Internet Crime Center received nearly 800,950 cybercrime complaints, representing potential total losses of more than $10.2 billion.
In the face of these statistics, cybersecurity is becoming increasingly important to businesses of all types, and the commercial lighting industry is not immune to these concerns. In particular, fear that hackers could use networked lighting control (NLC) systems to access building data such as occupancy patterns — or even business data such as customer information — is a significant reason why NLC installation continues to lag, despite research showing the technology’s significant potential to increase the energy savings of LED lighting.
Viewing cybersecurity of NLCs as vital to their market adoption, the DesignLights Consortium (DLC) included measures aimed at protecting networked systems from malicious attacks in the most recent version of its NLC Technical Requirements (NLC5). Products must meet these specifications for inclusion in the NLC Qualified Products List that guides scores of commercial and industrial lighting energy efficiency programs across North America.
The DLC is not a security standards body, and it doesn't develop security standards. Through research and outreach, however, it has identified several cybersecurity standards and services that satisfy the NLC5 criteria, and has developed a resource to help manufacturers and other users find standards and/or services appropriate to each situation. The following are cybersecurity standards and services recognized by the DLC.
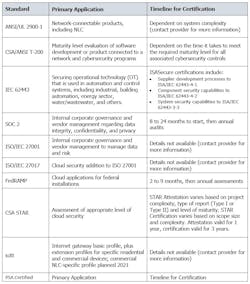
This table describes the primary application and timeline for certification of the cybersecurity standards listed in Table CS-1 of the DLC NLC5 Technical Requirements.
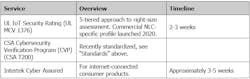
This table describes an overview and timeline for the cybersecurity services listed in Table CS-2 of the DLC NLC5 Technical Requirements.
Increasing the cybersecurity of NLCs will enhance their value for both utilities and end-users, helping to accelerate adoption of a game-changing and as-yet under-utilized technology.
Levin Nock is Senior Technical Manager for the DesignLights Consortium.