Electrical power is so intrinsic to our daily lives, it is easy to take it for granted. But as digitalization accelerates across all sectors and applications, so does electrification. You can’t have digital transformation without electrification. When an application is critical, such as a hospital, airport, or industrial control system, the supporting electrical infrastructure automatically becomes mission-critical. This, in turn, means cybersecurity measures should be in place to prevent power system disruptions that could impact the uptime of those critical applications.
Cybersecurity is often associated with data and information technology (IT) personnel, but the traditional responsibilities of IT and operational technology (OT) teams are steadily converging as equipment connectivity and electrification increase in critical environments. This means facility managers and OT engineers need to understand more about networking and systems administration, while IT teams must know more about the types of technology they use and its availability needs.
When defining the responsibility of managing OT cybersecurity, it is first important for an organization to ensure electrical safety and reliability are not an oversight. This means employing personnel or trusted third parties who fully understand electrical safety codes and standards in addition to a facility’s technology, connectivity systems, critical processes, and cybersecurity risks. In this article, the importance of electrical safety as it relates to OT cybersecurity will be explained by exploring:
- Electrical safety risks of securing OT,
- The essential role of qualified workers, and
- Safe management of OT cybersecurity.
What are the electrical safety risks of securing OT?
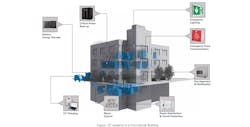
OT networks monitor and ensure the safety of building and facility infrastructure that operates critical processes, including motor controls, power distribution and projection, fire detection systems, and more (see the Figure below). When these systems and components are networked for monitoring, data collection, and insights, they can form an attack surface from which cybercriminals can gain access.
An IT security professional who has not completed proper training on handling electrical equipment or been through a facility safety briefing does not have the requisite preparation to make informed decisions when it comes to securing these environments.
Unlike today’s cutting-edge IT networks, OT systems often contain a mix of legacy and modern equipment. In the past, OT equipment was simply cut off or “air-gapped” from all communication networks to minimize vulnerability. Today, operational technology needs to be connected to broader communication networks to support more informed, real-time decisions.
This means cybersecurity professionals can be required to open energized electrical enclosures to capture network traffic or update the firmware. Interacting with energized equipment is a high-risk activity, requiring a thorough understanding of electrical safety codes and standards outlined by the National Fire Protection Association (NFPA) in the following documents:
- NFPA 70 (2020), National Electrical Code (NEC)
- NFPA 70E (2021), Standard for Electrical Safety in the Workplace
- NFPA 70B, Recommended Practice for Electrical Equipment Maintenance
NFPA 70E includes requirements for safe work practices to protect personnel by reducing exposure to major electrical hazards, including shock, electrocution, arc flash, and arc blast. These requirements rely on proper installation (per the NEC) and maintenance (performed per NFPA 70B).
NFPA 70B also covers critical requirements for safely accessing and evaluating many common OT technologies, such as motor controls, automatic transfer switches, and more. It provides guidance on topics such as:
- Required personal protective equipment
- Safety/hazards assessment
- Safety instrumented systems
- Lockout/tagout and safe work procedures
- Common failure modes for equipment under control
It typically takes upward of a year of in-person training and support before maintenance professionals are prepared to safely work on or around energized equipment on their own. It seems logical this requirement should also apply to professionals tasked with securing OT networks and systems.
Why are qualified workers so important?
Traditionally, trained cybersecurity personnel are well-versed in the system characteristics of confidentiality, integrity, and availability — but they are not trained to operate with electrical safety and system reliability in mind. This challenge goes both ways. For example, electrical engineers aren’t often taking classes on cybersecurity, and cybersecurity personnel aren’t often trained on electrical safety.
Addressing cybersecurity on OT networks requires comprehensive cross-functional consideration and typically is not the responsibility of any single discipline or entity within an organization, resulting in distributed or ambiguous ownership.
Specific real-time consideration of the availability, performance, safety, and other needs of the system should be considered. Often, given the embedded nature of components in these networks, typical IT methods, tools, and policies are either not effective or can damage the system. Scanning a system of laptops and workstations with a tool designed for these assets is different than scanning a network of controllers and other embedded devices. The impact of improper interaction with these systems can range from a device failure or process disruption to random data dumped onto a network.
So, how do you address safety and cybersecurity for OT systems?
A solution for safely managing OT cybersecurity
There is an essential need to advance safety, reliability, and cybersecurity throughout the entire life cycle of the facility. The ability to safely assess, interact, and harden the equipment found in critical power systems helps minimize risk to personnel and reduces the likelihood of downtime.
For example, a failure in physical processes used to evaluate the cybersecurity of critical power system architecture can result in a direct failure in the critical application. Extreme efforts are made at the design, build, and operational phases to ensure continuous operation and reliability in critical environments. Electrical infrastructure is complex and requires highly qualified personnel to secure it. If an individual is not familiar with the basic principles of electrical safety, accidents are more likely and can result in personal injury and downtime.
Therefore, action items for personnel tasked with the OT cybersecurity of any operation should include the ability to:
- Inventory all connected hardware, software and dataflows.
- Assess facility OT networks and assets to evaluate the attack surface and discover known vulnerabilities and weaknesses.
- Understand critical processes and how cybersecurity processes could negatively impact uptime.
- Evaluate the electrical safety codes and requirements associated with life-cycle cybersecurity maintenance to support personnel safety, uptime, and compliance.
Together, these tasks require comprehensive knowledge of:
- OT and ICS applications and processes
- Electrical safety codes and standards
- Electrical reliability and uptime
- Industrial network defense
- Cybersecurity regulation and guidance
- Cybersecurity assessment and vulnerability detection
- Defensive technologies and approaches
- Life-cycle cybersecurity maintenance
Prioritizing safe life-cycle security for critical systems
Cybersecurity risks to connected systems have never been greater, as malicious threat actors look to exploit system vulnerabilities, which often exist on electrical system assets with the least cybersecurity oversight.
To address these potential vulnerabilities, critical industries require expertise in power systems engineering and cybersecurity. The goal is to safely assess, interact, and secure critical power system networks without risking the safety of personnel or uptime of critical processes. This is complex and requires in-depth training and experience.
At the end of the day, the most important thing is protecting what matters: your personnel, data, and critical processes.
Anthony Ciccozzi is an industrial control system cybersecurity specialist who is responsible for leading cybersecurity product assessments for the Secure Development Lifecycle (SDLC) process at Eaton. He can be reached at [email protected].
About the Author
Anthony Ciccozzi
Anthony Ciccozzi is an industrial control system cybersecurity specialist who is responsible for leading cybersecurity product assessments for Eaton’s Secure Development Lifecycle (SDLC) process. He provides internal consulting for cybersecurity as it relates to embedded systems, distributed energy systems, communication and control applications, and UL, NERC CIP, and NIST Risk Management Framework (RMF) compliance programs. He can be reached at [email protected].